Endpoint protection is table stakes for any organization.
For cyber criminals printers, multifunctional devices and any other office equipment having contact with the outside is the low hanging fruit and can become the first target for exploitation in the pursuit of breaching a company’s perimeter. The good news is that Canon imageRUNNER ADVANCE multifunctional devices include extensive security features to help an organization “harden” their print fleet.
These risk mitigation actions can include closing un-used communication ports, encrypting hard disk drives and data flow protocols which are designed to help minimize the exposure of networked devices. Our expert field engineers can help you take steps to protect your document workflow without compromising the productivity and efficiency of your workforce.

Security Measures to Protect against Malware and Tampering
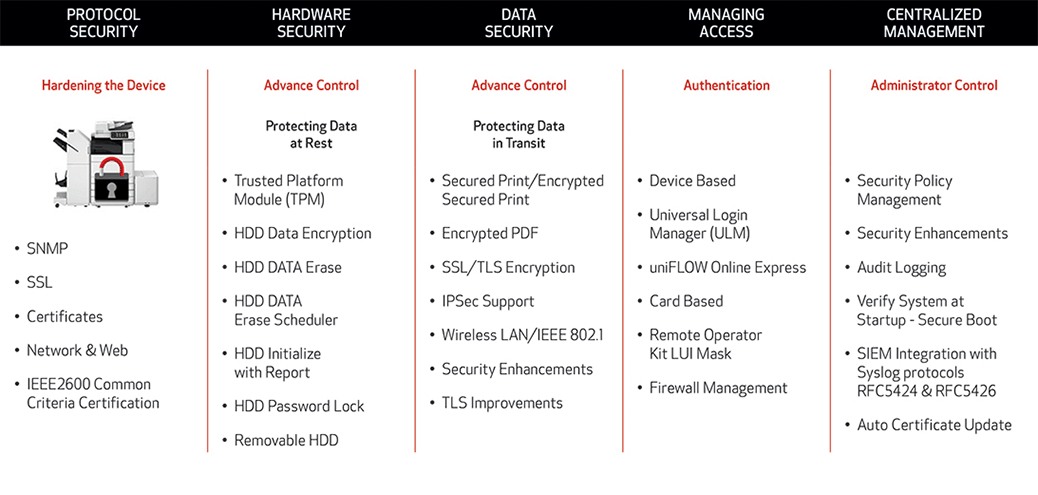
Protocol Security - Hardening the Device
Throughput has always been paramount to an efficient document capture process and output workflow. In today’s environment, secure throughput architecture is even more critical. Administrators should ensure that MFP device protocols are configured to help minimize the risk of a breach at the device.
For more information or to request Device Hardening Services please contact us today or click here to have someone contact you.
Note: Canon imageRUNNER ADVANCE Third Generation devices meet the IEEEE2600 Common Criteria.

Hardware Security - Protecting Data at Rest
Today most MFP systems hard disk drive (HDD) protection features offer several options to keep data safe. An example of this would be a tamper proof Trusted Platform Module (TPM) and HDD Data Encryption to help ensure that your data is encrypted before storing it on the resident hard drive. Take advantage of the extended HDD options to protect data at rest on the device.
- HDD Data Erase – Delete Job Data after each task by overwriting the null data or random data. Deletion Mode: Once with null data, Once with random data, 3 times with null data, or the DoD standard
- With a HDD Data Erase Scheduler (Optional) you can set a daily, weekly and monthly schedule for overwriting temporary data on HDD
- HDD Initialize – Overwrite modes supported for the HDD Initialize function include:
- Overwrite once with null (default)
- Overwrite once with random data
- Overwrite three times with random data
- Overwrite three times in the following order (DoD Standard)
- Fixed value
- Complement number of fixed value
- Random data
- Overwrite nine times with random data
- A removable HDD allows system administrators to physically lock and unlock and remove the device’s internal HDD
Data Security - Protecting Data in Transit
Just as important as protecting data at rest, is protecting it while in transit. These security features can help protect data while it travels from the user’s workstation or mobile device to a printer:
- Encrypted Secured Print and Secured Print are print functions that hold a job in queue until the user enters the appropriate password at the device
- The Encrypted PDF feature of most MFD systems can support 40-bit/128-bit RC4 encryption and 128-bit AES (Advanced Encryption Standard) for greater security when sending documents
- IP Sec helps ensure the privacy and security of information sent to and from the device, while in transit over unsecured networks
- Wireless LAN supports the latest wireless encryption standards, including WEP, WPA and WPA2. IEEE 802.1 is the standard protocol for port-based Network Access Control
- Check for key SSL Certificate Improvements
- TLS improvements enable administrators to specify TLS versions for encrypted communication
Controlling Access
Controlling access of MFD system users is the first line of defense. Most devices provide options that let administrators define user profiles and provide various levels of what features and functions an individual is authorized to use (i.e., printing and copying only; print, scanning, copying and faxing, etc.).

Centralized Management
For administrators a centralized management option helps to contain costs, assists with maintaining an ideal security posture, helps monitor devices and user behavior and can be used to provide an audit platform that may help comply with regulatory dependencies. Other control features include:
- Security Policy Management
- Secure Booting of the device for firmware integrity
- Automatic Certificate Updates
- Security Information and Event Management (SIEM) Integration





